- Accueil
- Actualités et public…
- Publications
- Review of UK cyber r…
- Sur cette page
25 mars 2022
Review of UK cyber resilience regime: Tougher rules for outsourced services proposed
The government has announced a review of the UK cyber security regime, that could see its scope dramatically widened, as well as increase the level of supervision over certain digital service providers. In particular, the proposed extension to providers of a broad range of "managed services" could bring a wide range of outsourced service providers in-scope of the cyber-security requirements for the first time.
On 19 January 2022, the government published two open consultations: "Proposal for legislation to improve the UK's cyber resilience", and a separate consultation on "Embedding standards and pathways across the cyber profession by 2025". Taken together, the two consultations seek to respond to gaps in the existing framework for cyber risk and resilience in the UK.
Recent high-profile cyber-attacks, such as the December 2020 SolarWinds supply chain compromise and the July 2021 ransomware attack on managed service provider Kaseya, demonstrate how malicious actors have been able to compromise activities and cause disruption throughout the wider economy. The government recognises the threat that cyber security risks pose to businesses, but also to the critical infrastructure that supports the UK economy and national security. The existing UK Network and Information Systems Regulations 2018 (NIS Regulations) has formed a key part of its approach to managing risks to critical infrastructure, alongside other sectoral regulatory frameworks. However, the cyber threat landscape is evolving all the time. As such, the government considers it critical to ensure that the NIS Regulations can remain effective in increasing cyber resilience going forward.
This briefing focusses on the first proposals for legislation to improve the UK's cyber resilience regime. It will be relevant to all organisations within scope of the current NIS Regulations (whether as digital service providers (DSPs) or operators of essential services (OESs), as well as other private and public entities that provide digital and other managed services that an essential service relies on.
Summary of the proposed measures
- Expand the scope of ‘digital services’ in-scope to include a broad range of certain ‘managed services’.
- Apply a two-tier supervisory regime for all DSPs: a new proactive supervision tier for the most critical providers, alongside the existing reactive supervision tier for other in-scope DSPs.
- Create new delegated powers to enable the government to update the NIS Regulations, both in terms of framework but also scope, with appropriate safeguards.
- Create a new power to bring certain organisations, that entities already in scope are critically dependent on, within the remit of the NIS Regulations.
- Strengthen existing incident reporting duties, currently limited to incidents that impact on service continuity, to also include other significant incidents.
- Extend the existing cost recovery provisions to allow regulators (including Ofcom, Ofgem, and the ICO) to recover the entirety of reasonable implementation costs from the NIS companies that they regulate.
- Standardise the cyber security profession, including potential oversight of the profession under a legislative scheme (subject to a separate consultation).
Proposals to amend provisions relating to digital service providers (DSPs)
Expanding the regulation of DSPs, including to 'managed services'
Providers of digital managed services (such as security monitoring, managed network services or business processing outsourcing) play a central role in supporting many organisations and essential services in the UK. These providers are an attractive target for malicious threat actors, who can seek to use them to compromise multiple organisations at scale. As such, the government identified that the most critical managed service providers may be a source of systemic cyber risk, yet the majority are currently outside of the NIS Regulations. The government wants to ensure that providers who frequently have privileged access and provide critical support to essential UK services have adequate cyber security protections in place, and can be regulated effectively.
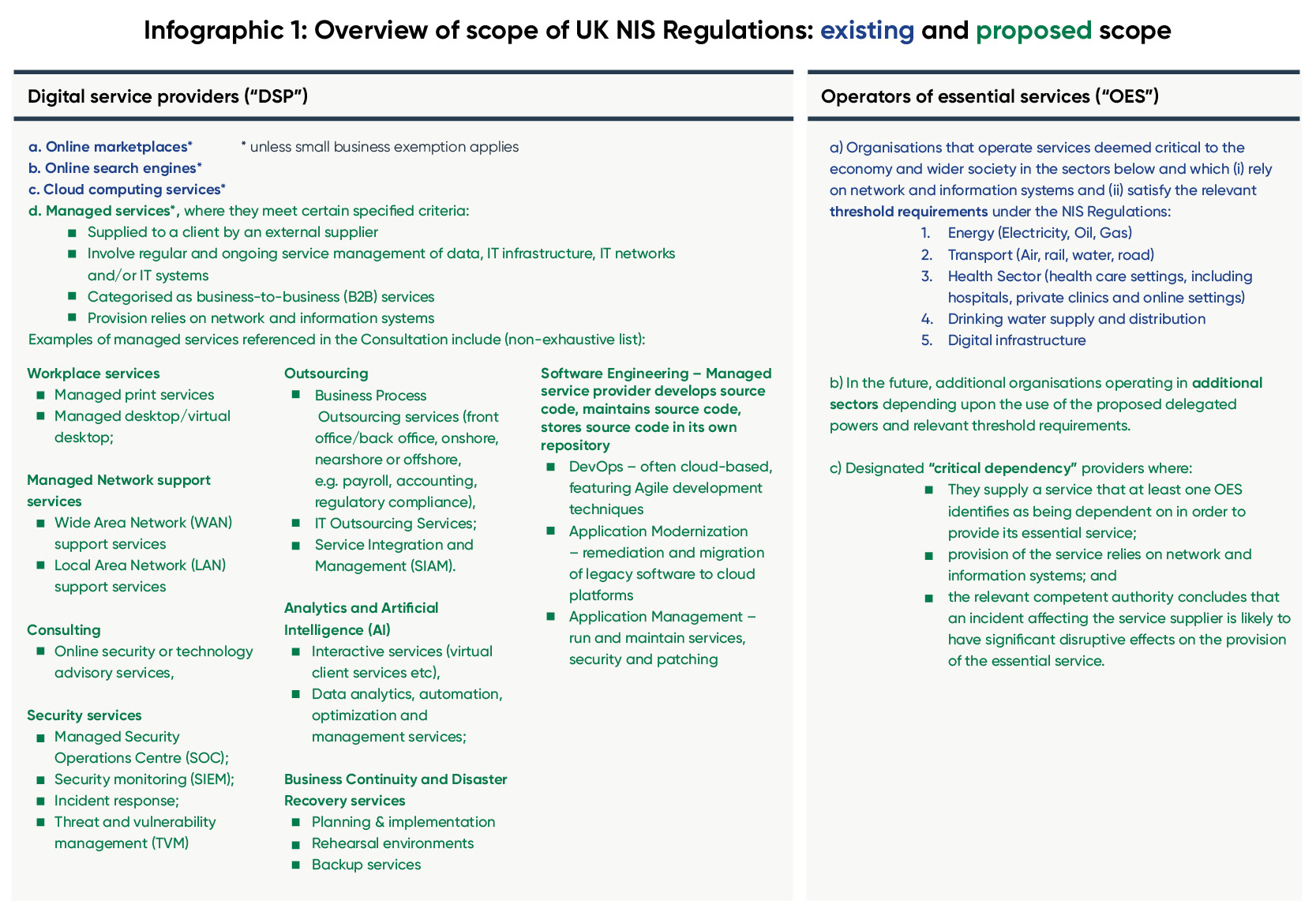
Currently, regulation of DSPs under the NIS Regulations includes online marketplaces, online search engines and cloud computing services (in each case, subject to an exemption for certain small businesses that do not meet the relevant thresholds relating to turnover, number of employees etc) – see our earlier briefingon the scope of the NIS Regulations.
The proposals would extend the scope of DSPs to also include "managed services"; no definitive list of services is provided, although a non-exhaustive list of examples (see Infographic 1) suggests this is very broad. Providers would only be in-scope where the managed services meet certain characteristics:
- supplied to a client by an external supplier
- involve regular and ongoing service management of data, IT infrastructure, IT networks and/or IT systems
- categorised as business-to-business (B2B) services
- provision relies on network and information systems.
Given the potential breadth of this definition, the government is exploring options to narrow the scope, including through further risk-based characteristics, to focus on those managed services where disruption would have the most substantial impact on the UK's cyber resilience. For example, alongside the above characteristics, the service would have to:
- have privileged access or connectivity to a customer's data, IT infrastructure, IT networks and/or IT systems
- perform essential or sensitive functions, such as the processing and/or storage of confidential or business-critical data.
The exemption for small businesses would apply to managed service providers (as with other DSPs), but the government is also exploring whether this exemption remains appropriate (see below).
What obligations would these managed services be subject to?
These managed services would be subject to the same duties as other DSPs under the NIS Regulations, i.e. requiring them to register with the Information Commissioner (as the relevant competent authority) and have appropriate and proportionate security measures to ensure that their own network and information systems are secure. They would also be required to report relevant incidents to the Information Commissioner. For international companies, the requirement to designate a UK representative would also apply. As with other NIS Sectors, further detail on the nature of supervision and security expectations would be determined by the ICO through guidance.
Consideration of DSP exemption for small and micro-businesses
The current exemption for small and micro-businesses would apply to managed service providers, but the government is considering if this blanket exemption is still proportionate.
Currently, DSPs are exempted from the NIS Regulations if they have fewer than 50 staff, turnover of below €10m, or a balance sheet total of below €10m per year. Whilst the government recognises the need to minimise regulatory burdens on small and micro-businesses, it notes that recent incidents have highlighted the risks associated with managed service providers, regardless of their size. It is therefore considering whether this blanket exemption is still proportionate to the risk. One alternative might be for specific small and micro-business to be exempt only where they are specifically exempted by the relevant competent authority.
Organisations providing managed services and which fall below the employee, turnover, and balance sheet thresholds under the current exemption might therefore consider engaging with the consultation.
Two-tier supervisory regime for DSPs, depending upon criticality and systemic risk
The proposals recognise the wide variety and number of DSPs operating multiple services within the UK economy, and that some of these present higher cyber risks than others. The government therefore proposes a two-tier regime, depending upon the degree of risk and systemic dependencies:
- For the most critical DSPs, a pro-active (ex ante) supervisory regime. A limited group of the most critical DSPs would be required to more actively demonstrate that they have fulfilled their duties under NIS, and cooperate with the ICO to ensure compliance. This would include information gathering and inspection powers when necessary.
- For the remaining DSPs under the NIS Regulations, reactive (ex-post) supervisory regime. These DSPs would need to comply with the same cybersecurity requirements under the NIS Regulations, but under a lighter-touch supervisory regime; the ICO would only take regulatory action where there has been an incident, or a credible report of an incident or a failure to implement the requirements.
The government is proposing several options for the criteria to identify the most critical and systemic providers, including consideration of factors relating to the provider itself (e.g. market reach, scale of service provided, and concentration in the market) as well as characteristics of their customers (e.g. degree of criticality of services supplied, level of dependence, and likely consequence of failure). The criteria would not be defined in detail in legislation, but would instead provide flexibility for the criteria to be adapted as the security context evolves. Cross-sector collaboration may also be necessary with other sectors, such as financial services, where digital services play a critical role. The government notes, however, that the ICO would retain the right to designate DSPs that fall outside of this criteria.
The consultation sets out a proposed list of factors as examples of how these criteria might be applied in practice. Providers of digital or managed services who might have the characteristics to be subject to the more pro-active supervisory regime might therefore wish to consider the consultation questions on the proposed criteria.
Future-proof the UK's existing cyber security legislation, primarily the NIS Regulations
Given the rapidly evolving cyber security landscape, the government considers it imperative that the NIS Regulations remain relevant, up-to-date and sufficiently agile.
Currently, changes (however small) to the NIS Regulations can only be made through primary legislation. The proposal therefore seeks to provide ministers with delegated powers to make changes through secondary legislation, subject to certain restraints and limitations (expansion of its fundamental principles and purpose would not be covered). The power would be subject to safeguards (although details are yet to be provided), as well as a duty to consult on any proposed changes; as some amendments may be security-sensitive, alongside any public consultation, the government may decide to consult OESs and DSPs separately (and in confidence, so as not to jeopardise their security).
Delegated power to amend sector coverage of NIS Regulations
Aside from the inclusion of "managed services" as a digital service, the government is not proposing any further sectors that would become part of the NIS framework at this stage. However, it recognises there may be a need to add other sectors in the future in areas where the UK may be exposed to increased cyber security risks. Illustrative examples referenced include electric chargepoint operators and data centres. The government is therefore proposing a delegated power to vary the sectors and sub-sectors that are in-scope, including evidence gathering powers and appropriate safeguards. Sector-specific engagement would precede any proposed extension.
Critical dependencies: Powers to designate "critical" suppliers or services with sectoral dependencies
The government would be granted a power to designate certain entities as "critical dependencies", which would have to comply with the same duties as OESs. These would be entities that are not themselves OESs, but upon which NIS sector entities are dependent. The consultation gives the example of IT service providers in the healthcare sector (although emphasises that this is an illustrative example only); outsourced IT services are not directly subject to the NIS Regulations as an OES as they do not provide healthcare services. However, a significant disruption of such outsourced IT services would very likely have direct and substantial impacts on the underlying healthcare provider. The services in question might also go beyond 'digital services' and refer, for example, to the continuous supply of a consumable resource such as a raw material relied upon by an NIS sector.
Under the proposals, the minimum requirements to be considered a 'critical dependency' are:
- the organisation must supply a service that at least on OES identifies as being dependent on in order to provide its essential services
- the provision of the service must rely on network and information systems
- the relevant competent authority must conclude that an incident affecting the supply of that service by that person is likely to have significant disruptive effects on the provision of the essential service.
Measures would be implemented to support proportionality and consistency across sectors, including guidance on minimum criteria and factors to be considered by authorities when identifying critical dependencies, and guidance on sectoral assessments and industry engagement.
The consultation also notes that critical dependencies can arise in the wider supply chain, especially where there are a limited number of suppliers who may not be easily interoperable or substitutable. The government, therefore, also proposes a power to designate organisations that are only deemed "critical" when their supply relationships are considered across multiple NIS sectors in aggregate.
OES incident notification requirements to extend beyond incidents affecting continuity of service
Currently, the NIS Regulations only require OESs to notify authorities of any incident "which has a significant impact on the continuity of the essential service that the OES provides". To date, the number of cyber security incidents reported under the NIS Regulations has been low, in stark contrast to the incident numbers known by the government. Although the government already has the ability to lower the thresholds for which incidents are reportable under statutory guidance, the NIS Regulations still limit this to those that affect continuity of service only. For example, ransomware attacks that do not affect the critical service would not be in-scope (although where they involve breaches of personal data will be subject to reporting under UK GDPR.
Voluntary schemes for reporting of cyber incidents are already in place, but the government notes that uptake has been very limited. The consultation explains that early reporting of such incidents could enable the authorities to take appropriate action, including supporting other operators who may be vulnerable to the same type of attack.
The proposed new incident reporting requirement is therefore as follows:
"Any incident which has a significant impact on the availability, integrity, or confidentiality of networks and information systems, and that could cause, or threaten to cause, substantial disruption to the service."
Setting the appropriate threshold for reporting is vital; the government has no wish to overburden operators or competent authorities with the need to report every potential threat. For each sector, sector-specific thresholds for reporting would be set out in guidelines by the relevant competent authorities, seeking to identify only the more serious and threatening incidents.
Note that DSPs are subject to different incident reporting obligations to OESs; for DSP reporting thresholds, the government has already reported on amendments to the determination of which incidents are have a "substantial impact" – see our earlier briefing, here.
Full cost recovery for NIS functions
The government proposes that costs incurred by competent authorities for regulating and enforcing NIS should be recoverable from industry, rather than the taxpayer. It is consulting on various options, including recovering costs incurred from specific measures after regulatory action has taken place, or a 'hybrid' cost recovery model, to also enable recovery on an ongoing fee basis.
All organisations that are currently in-scope of the NIS Regulations (or may be in the future) might therefore be interested in the consultation's questions on the proposed cost recovery model.
Considerations for the standardisation of the cyber security profession
The government recognises that cooperation between DWPs and their customers is a necessary and complementary step in order to effectively manage cyber resilience. DSPs must fulfil their duties to protect essential services, but their customers also need to have the right tools and information to make informed decisions.
Alongside the proposal on the NIS Regulations, the government also published a separate consultation on embedding standards and pathways across the cyber profession. Whether further guidance on supplier-customer cyber resilience cooperation is necessary, in particular regarding those 'critical' DSPs subject to the more proactive supervisory regime.
EU: Proposals for NIS2 Directive
In parallel to the proposed changes to the UK NIS Regulations, businesses operating in the EU should also be aware of the European Commission's Proposal for a directive to replace the current NIS Directive with a revised directive, "NIS2". The requirements and changes under the Proposal are wide ranging and beyond the scope of this briefing.
Challenges for businesses
Many of the cyber resilience requirements under the NIS Regulations are simply good practice, such as the requirement to implement appropriate and proportionate technical and organisational measures to manage risks and minimise impacts on incidents affecting network and information systems. However, the proposals to extend and future-proof the NIS regime could have significant implications for in-scope businesses. In particular:
- The broad definition of "managed services" in the legislation, and wide range of illustrative examples listed, means that a wide range of organisations might be in-scope. The element of subjectivity in some of the criteria might also make it difficult for businesses to work out if they need to comply or not.
- Small businesses providing digital services may find the NIS cyber resilience requirements burdensome and may wish to comment on the potential revision to the exemption for small and micro-businesses.
- DSPs operating in both the UK and EU will be subject to divergent regimes, including divergent incident notification requirements.
- Alongside the NIS regime, sector specific requirements are likely to raise cyber resilience expectations in certain sectors, in particular in financial services – see our earlier briefings on the UK and EU developments on operational resilience in financial services.
- The extension to the incident notification requirements for OESs is likely to broaden the type of incidents that need to be reported.
- The proposed full cost recovery model could expose businesses to potentially high costs for supervision under the NIS Regulations, in addition to wider costs associated with cyber incidents.
At this stage, the proposals only describe the intended changes, without setting out any proposed legislation or detailed requirements. However businesses, both those who might be in-scope of the revised NIS Regulations and those who may be affected by cyber incidents propagated in other organisations, may wish to respond to the consultation by the 10 April 2022 deadline to make their views heard.
The separate consultation on the cyber security profession has a different closing date of 20 March 2022.
Related Insights

A call for co-operation: IOSCO and ESMA look to enlist the support of platform providers in combatting online harm
par Clare Reynolds et Neil Millar

Our survey says … Building cyber resilience in the financial sector
par plusieurs auteurs

Marks & Spencer and Co-op cyber attacks
par Jo Joyce et Clare Reynolds


